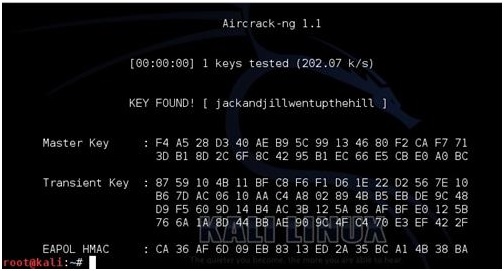
What happened?
In May 2014, FCC Chairman Tom Wheeler released a plan that would have allowed companies like AT&T, Comcast and Verizon to discriminate online and create pay-to-play fast lanes.
Millions of you spoke out — and fought back.
Thanks to the huge public and political outcry, Wheeler shelved his original proposal, and on Feb. 4, 2015, he announced that he would base new Net Neutrality rules on Title II of the Communications Act, giving Internet users the strongest protections possible.
The FCC approved Wheeler’s proposal on Feb. 26, 2015. This is a watershed victory for activists who have fought for a decade to protect the open Internet.
However, now that the FCC’s Net Neutrality rules are out in the world, opponents are doing everything they can to undermine the open Internet.
What is Net Neutrality?
Net Neutrality is the Internet’s guiding principle: It preserves our right to communicate freely online. This is the definition of an open Internet.
Net Neutrality means an Internet that enables and protects free speech. It means that Internet service providers should provide us with open networks — and should not block or discriminate against any applications or content that ride over those networks. Just as your phone company shouldn't decide who you can call and what you say on that call, your ISP shouldn't be concerned with the content you view or post online.
Without Net Neutrality, cable and phone companies could carve the Internet into fast and slow lanes. An ISP could slow down its competitors' content or block political opinions it disagreed with. ISPs could charge extra fees to the few content companies that could afford to pay for preferential treatment — relegating everyone else to a slower tier of service. This would destroy the open Internet.
Who's attacking Net Neutrality?
Net Neutrality opponents are working everywhere from Congress to the courts to dismantle or undermine the FCC’s Title II classification. In the wake of the February ruling, 10 lawsuits designed to gut Net Neutrality have been filed (Free Press has
jumped in to defend the rules) and legislators have
introduced numerous deceptive bills that would demolish these protections. Most recently, the attack in Congress has come from the appropriations committees. Both the House and Senate committees have passed bills containing riders that would
sabotage the Net Neutrality rules.
What does ‘reclassify’ mean?
When Congress enacted the
1996 Telecommunications Act, it didn’t want the FCC to treat websites and other Internet services the same way it treats the local access networks that enable people to get online. Congress understood that the owners of the access networks have tremendous gatekeeper power, and so it required the FCC to treat these network owners as “common carriers,” meaning they couldn’t block or discriminate against the content that flows across their networks to/from your computer.
However, in a series of politically motivated decisions first by FCC Chairman Michael Powell (now the cable industry’s top lobbyist) and then by FCC Chairman Kevin Martin, the FCC decided to classify broadband Internet access service as an “information service,” meaning that the law sees it as no different from a website like freepress.net or an online service like LexisNexis. These decisions removed the FCC’s ability to prohibit ISPs from blocking or discriminating against online content (it also removed the FCC’s ability to ensure that ISPs protect your privacy).
In Verizon vs. FCC, the court stated that the FCC lacks authority because of “the Commission’s still-binding decision to classify broadband providers not as providers of ‘telecommunications services’ but instead as providers of ‘information services.’”
On Feb. 26, the FCC voted to define broadband as what we all know it is — a connection to the outside world that is merely faster than the phone lines we used to use for dial-up access, phone calls and faxes.
Doing so gave the agency the strongest possible foundation for rules prohibiting discriminatory practices.
What did the FCC vote on?
The new rules, rooted in Title II of the Communications Act, ban throttling, blocking and paid prioritization.
Why is Net Neutrality important for businesses?
Net Neutrality is crucial for small business owners, startups and entrepreneurs, who rely on the open Internet to launch their businesses, create a market, advertise their products and services, and distribute products to customers. We need the open Internet to foster job growth, competition and innovation.
Net Neutrality lowers the barriers of entry for entrepreneurs, startups and small businesses by ensuring the Web is a fair and level playing field. It’s because of Net Neutrality that small businesses and entrepreneurs have been able to thrive on the Internet. They use the Internet to reach new customers and showcase their goods, applications and services.
No company should be able to interfere with this open marketplace. ISPs are by definition the gatekeepers to the Internet, and without Net Neutrality, they would seize every possible opportunity to profit from that gatekeeper control.
Without Net Neutrality, the next Google would never get off the ground.
Why is Net Neutrality important for communities of color?
The open Internet allows communities of color to tell their own stories and to organize for racial and social justice.
The mainstream media have failed to allow people of color to speak for themselves. And thanks to economic inequality and runaway media consolidation, people of color own just a handful of broadcast stations. The lack of diverse ownership is a primary reason why the media have gotten away with portraying communities of color stereotypically.
The open Internet gives marginalized voices opportunities to be heard. But without Net Neutrality, ISPs could block unpopular speech and prevent dissident voices from speaking freely online. Without Net Neutrality, people of color would lose a vital platform.
And without Net Neutrality, millions of small businesses owned by people of color wouldn't be able to compete against larger corporations online, which would further deepen the economic inequality in our nation’s most vulnerable communities.
What is the history of Net Neutrality at the FCC?
The
FCC’s 2010 order was intended to prevent broadband Internet service providers from blocking or interfering with traffic on the Web. The Open Internet Order was generally designed to ensure the Internet remained a level playing field for all — that's the principle we call Net Neutrality (we say “generally,” since the FCC’s rules prohibited wired ISPs from blocking and discriminating against content, while allowing wireless ISPs to discriminate against but not block websites).
In its January 2014 ruling, the court said that the FCC used a questionable legal framework to craft the Open Internet Order and lacked the authority to implement and enforce those rules.
The court didn't comment on the merits of the rules. Instead, it
ruled against the FCC's ability to enforce Net Neutrality under the shaky legal foundation it established for those rules. The court specifically stated that its “task as a reviewing court is not to assess the wisdom of the Open Internet Order regulations, but rather to determine whether the Commission has demonstrated that the regulations fall within the scope of its statutory grant of authority.”
When the FCC made its 2010 open Internet rule, it relied on two decisions the Bush-era FCC made, rulings that weakened the FCC’s authority over broadband Internet access providers. Nothing in the January 2014 court decision prohibited the FCC from reversing those misguided decisions and reclassifying ISPs as common carriers.
In fact, both this decision and a
prior Supreme Court decision showed that reclassification would provide the best means of protecting the open Internet.
So what can we do now?
The cable and phone companies — and their allies in Congress — willl do everything they can to dismantle the big win at the FCC in February 2015.